29 June 2020
With a steadily rising frequency of spear phishing, business email compromise and other attacks on corporates, the chief information security officer is everyone’s new best friend, report Wade Bicknell and Vanessa Riemer.
“Never let a good crisis go to waste,” is among the many pithy pieces of advice bequeathed us by Winston Churchill. It’s unfortunate that what was a maxim originally offered to politicians has also been adopted by fraudsters, ever ready to exploit the opportunities created by sudden events.
If the economic carnage wrought by the coronavirus crisis wasn’t enough for governments and businesses to contend with, recent weeks have brought reports of financial institutions and corporates being targeted by sophisticated criminals employing a variety of techniques to initiate payments purportedly relating to the pandemic. Google is reported to have set up a Covid-19 task force, whose priorities include preventing unemployment benefit scams.
Both pre-coronavirus and since the outbreak began, social engineering, business email compromise and vendor payment targeting have been among the favourite techniques employed by bad actors to fraudulently initiate payments. These techniques are accompanied by newer tactics that target treasury management and accounts payable teams with scams attempting to deploy malware to corrupt account information and reroute payments to fraudulent accounts or to steal proprietary information to extort money.
To support its clients in fending off such attacks, Deutsche Bank issued the notice Warning of cyber attacks related to the coronavirus pandemic in April, providing information to clients on how to identify the scam e-mails, text messages and social media posts that have been spawned by the Covid-19 crisis. More recently, cybersecurity and fraud prevention were discussed in several webinars across the globe hosted by the bank.
A sequence of scams
Like its peers, Deutsche Bank engages with its clients regularly on relevant security topics. Since Covid-19 moved from a local to a global issue, the bank has alerted clients to cyber criminals masquerading as reputable authorities who exploit the fear and uncertainty triggered by the pandemic by using business email compromise (BEC), text messages and social media posts purporting to provide information on the coronavirus.
These types of fraudulent messages are used to entice a company’s employees to reveal sensitive information, such as log-in data for online accounts, credit card details and mobile phone numbers through fake websites. In some cases, individuals are invited to click on attachments or links, which promptly infect their computer or smartphone with malware that could access sensitive data or encrypt it for the purpose of extortion.
Industry information suggests a steady increase in the incidence of attempted and successful payment frauds and cyber threats. The US Federal Bureau of Investigations (FBI) has stated that losses resulting from business email compromise (BEC) alone reaches into the billions of dollars. Recent reports give an estimated figure for 2019 from BEC losses of US$1.7bn. As reported cases of coronavirus began to rise steadily in early April, the FBI warned that BEC schemes using the pandemic as a cover were expected to rise further.
Cyber security is attracting greater attention and publicity as a result, in contrast to 20 years ago when the level of interest was minimal. The first recorded major ransomware attack spread by infected email attachments, dubbed CryptoLocker, did not make major headlines until 2013-14, when the perpetrators targeted more than 500,000 machines and reportedly extorted around US$3m from victims.
"The prevalence of payment fraud creates the need for dynamic transaction surveillance."
Yet while the pandemic appears to have triggered an increased awareness of the risk of cybercrime, the appreciation of the risks were apparent long before and Covid-19-themed attacks are just the latest variation in a series of spear phishing attempts. Communications issued by some perpetrators include a link that promises to take users to a map of coronavirus infection rates by region, and while the map may appear accurate, it is in reality a spear phishing link that enables criminals to gain access to the user’s computer. Another still popular spear phishing scam is a communication announcing that the user is owed money, with a link inviting him/her to submit a claim by clicking on the link or providing personal and financial details
In contrast to “the ‘big bang’ events of 2016 and 2017 such as WannaCry, when massive dollar amounts were stolen, the current trend is that bad actors are stealing lower amounts that are offset by the incidence of loss increasing. Criminals are blanketing organisations with less ambitious scams that seek to gain smaller amounts as it is becoming harder to launder larger ransom payments.

WADE BICKNELL
Chief information security officer for the Americas, Deutsche Bank
Go to Corporate Bank EXPLORE MORE
Find out more about products and services
Go to Corporate Bank Go to Corporate BankStay up-to-date with
Sign-up flow newsbites
Choose your preferred banking topics and we will send you updated emails based on your selection
Sign-up Sign-upSubscribe Subscribe to our magazine
flow magazine is published annually and can be read online and delivered to your door in print
Fraud prevention and detection
To put oneself in an active position and to become able to control the risk of fraud attacks, one has to understand how fraudsters behave. The invoice redirect technique – also called supplier fraud – is taken as an example to comprehend a fraudster’s actions step by step.
As outlined below in Figure 1, invoice redirect involves a company receiving an e-mail or another type of communication, purporting to come from a regular supplier and requesting that the company update their bank details. Often times, employees fail to recognise that it isn’t legitimate e-mail from their supplier because the e-mail closely resembles those regularly received from the supplier. Fraudsters usually observe their victim for a longer period of time and exploit their knowledge; for example by attacking when the boss is on holiday. This increases the challenge of recognising a fraud case and checking back with a trusted colleague. Often the incident is only detected weeks later when the supplier reveals that payment is still outstanding. Attempts for funds recovery place the onus on employees and financial institutions to enquire where the fraudulent payment went and if there are chances to recover the funds.
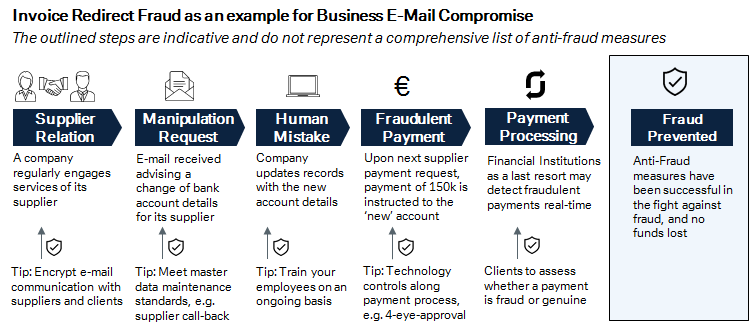
Figure 1
Source: Deutsche Bank
Given the tremendous global losses due to business e-mail compromise, prevention and detection have to go hand in hand and must also be a joint effort of financial institutions and corporations. Figure 1 outlines actions for corporates, which include well-known and very important basics like e-mail encryption and staff training. These two actions can prevent many cases of fraud attacks. E-mail encryption – knowing with whom you communicate by recognising their certificate – is an extremely helpful means for avoiding unwanted contacts from fraudsters. Similarly, given the high percentage of human involvement in fraud attacks, staff training is a key means in the fight against fraud. Lastly, applying technical controls like 4-eye-principle, 2-Factor authentication or call-back solutions for ensuring identity can strengthen these actions further.
The other side of the coin is financial institutions that process payment transactions. They are the last resort before a payment gets released and they have client-specific data at hand to apply automatic checks. While corporates can prevent fraud, financial institutions can detect it after a fraudulent payment was initiated but before the respective payment gets executed. This means that besides existing technical measures like secure communication and strong customer authentication, in future banks should take the next step and complement their services with intelligent payment fraud detection. Such detection should aim to assess not only payment details and individual payment history, but also device and behavioural irregularities via online channels, such as changes of geo location or browser version. A state-of-the-art customer service would enable corporates to get informed about such changes real-time or request for a hold or restriction of payments according to individual preferences and needs.
Such an extra layer of security offered by the banks, jointly with the effort within an organisation’s treasury and information security department, can create an encompassing protective shield going forward. Nonetheless it is important to understand there is no full protection against fraud attacks.
In addition to offering fraud prevention and detection services to their clients, banks should also step up their game in the protection of customer data. Deutsche Bank has established a comprehensive information and cyber security programme and organisation to implement controls and adhere to security policies and standards in accordance with evolving business requirements, regulatory guidance, and an emerging threat landscape.
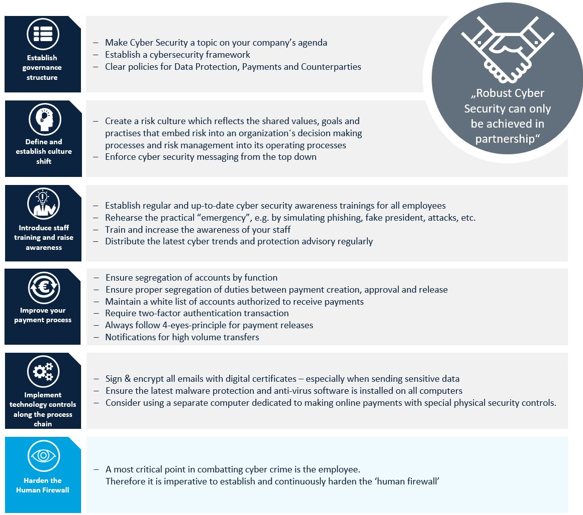
Figure 2: Top six recommendations to clients on cybersecurity
Source: Deutsche Bank
Future risk
While addressing current challenges, companies must also consider what risks might potentially become major ones in the future. The main threats can change very quickly as bad actors adapt their tactics in response to new preventive measures.
Current trends indicate a decoupling of business and technology to some extent. The outsourcing of some business processes is inevitably accompanied by a degree of risk. So ask yourself what intellectual property are you giving away? Remember that treasurers are often privy to information that should remain confidential. All of the traditional threats – including identity theft, ransomware attack and denial of service– will continue. And given that scenario, every employee’s new best friend is their company’s chief information security officer (CISO).
Wade Bicknell is Deutsche Bank’s chief information security officer for the Americas and Vanessa Riemer is product manager for cash transaction surveillance
You might be interested in
TECHNOLOGY
Technology versus virus Technology versus virus
Disruption caused by Covid-19 has pivoted the world towards technology to keep things moving. Some technologies have changed lives dramatically and their impact will endure beyond the pandemic. flow’s Janet Du Chenne examines how current tech trends could be managed to support a sustainable recovery
TECHNOLOGY, REGULATION
Beating Covid-19 cybercrime Beating Covid-19 cybercrime
With so many locked down at home in response to pandemic containment, the use of online services is exploding. But what is the risk to businesses? flow shares some tips to stay cyber-safe in a working from home environment
CASH MANAGEMENT
Safety twice Safety twice
With cyber-crime on the rise, and the implementation deadline under PSD2 for Strong Customer Authentication (SCA) in online payments coming up fast, banks and payment service providers are coming up with some innovative solutions. flow reports on what this means in practice



